Furry Friends Cause Trucking Border Delays At Canadian Border
To prevent reintroduction of rabies carried by dogs into the United States, new CDC regulations require proof of healthy pets at border crossing. Truckers who
We are a team of DOT Compliance and Licensing Professionals helping trucking and transportation companies remain safe, compliant, and profitable.
CNS or Compliance Navigation Specialists is DOT Compliance company that assists trucking and transportation companies remain DOT Compliant. We are part of a network of companies, CNS Companies, specializing in services related to the transportation, manufacturing, construction, service, education and medical industries.

A full-scale DOT Compliance Program managing a long haul carrier’s safety, compliance, licensing and more.
Learn more >>>
A DOT Compliance Program that keeps motor carriers compliant with the 6 Basic DOT Regulations required of all carriers.
Learn more >>>
Our Short-Haul/Construction Program is a full-scale program designed for private carriers that do not haul for-hire.
Learn more >>>
Our most comprehensive DOT Compliance Program, operating as your company’s off-site Safety Director or assisting your current safety personnel.
Learn more >>>
Our Non-CDL Program is a full-scale program managing safety, compliance, licensing and more for moving companies, couriers, landscapers, or any company subject to DOT regulations and does not employ CDL drivers.
Learn more >>>
Our DOT Audit Services cover a number of different types of DOT Audits that new and existing carriers will be subject to.
Our DOT Driver Services help trucking companies and carriers to stay compliant as they grow and hire more drivers.
Our DOT Vehicle Services focus on ensuring your vehicles are compliant with DOT Regulations, which is just as important as your drivers.
Our DOT Services for Special Carriers focus on companies outside of the typical motor carrier, like HAZMAT, Passenger and Bus Carriers.
CNS is part of a group of companies that offer other necessary services for the trucking and transportation industry, such as Commercial Trucking Insurance, CDL Training, Online Training Course, and even Healthcare.
Our DOT Licensing Services will cover you whether you are an existing company or just starting a trucking company. Our DOT Licensing Specialists can help you get up and running and in days with your DOT number, MC Authority, EIN, UCR, IFTA, 2290 HVUT, Fuel Taxes and can even set you up to get your Commercial Driver's License (CDL) with CNS Driver Training Center.
Our DOT Licensing Specialists will help you with every aspect of starting a trucking company. All you need to do is choose a name for your trucking company.
You will need to ensure your DOT Number, MC Authority, Vehicle Registration, etc. is all set up properly when you start your trucking business.
Our Licensing Specialists can help with all aspects of filing and renewing licenses, fuel taxes, etc.
CNS is part of a group of companies that offer other necessary services for the trucking and transportation industry, such as Commercial Trucking Insurance, CDL Training, Online Training Course, and even Healthcare.
To prevent reintroduction of rabies carried by dogs into the United States, new CDC regulations require proof of healthy pets at border crossing. Truckers who
CNS or Compliance Navigation Specialists is DOT Compliance company that assists trucking and transportation companies remain DOT Compliant. We are part of a network of companies, CNS Companies, specializing in services related to the transportation, manufacturing, construction, service, education and medical industries.
CNS Companies is a network of companies specializing in services related to the transportation, manufacturing, construction, service, education and medical industries. Our DOT Compliance division is handled by Compliance Navigation Specialists, CNS Insurance handles Commercial Truck Insurance, CDL training is managed by the CNS Driver Training Center and healthcare is managed by CNS Occupational Medicine.
We are a team of DOT Compliance and Licensing Professionals helping trucking and transportation companies remain safe, compliant, and profitable.
CNS or Compliance Navigation Specialists is DOT Compliance company that assists trucking and transportation companies remain DOT Compliant. We are part of a network of companies, CNS Companies, specializing in services related to the transportation, manufacturing, construction, service, education and medical industries.

A full-scale DOT Compliance Program managing a long haul carrier’s safety, compliance, licensing and more.
Learn more >>>
A DOT Compliance Program that keeps motor carriers compliant with the 6 Basic DOT Regulations required of all carriers.
Learn more >>>
Our Short-Haul/Construction Program is a full-scale program designed for private carriers that do not haul for-hire.
Learn more >>>
Our most comprehensive DOT Compliance Program, operating as your company’s off-site Safety Director or assisting your current safety personnel.
Learn more >>>
Our Non-CDL Program is a full-scale program managing safety, compliance, licensing and more for moving companies, couriers, landscapers, or any company subject to DOT regulations and does not employ CDL drivers.
Learn more >>>
Our DOT Audit Services cover a number of different types of DOT Audits that new and existing carriers will be subject to.
Our DOT Driver Services help trucking companies and carriers to stay compliant as they grow and hire more drivers.
Our DOT Vehicle Services focus on ensuring your vehicles are compliant with DOT Regulations, which is just as important as your drivers.
Our DOT Services for Special Carriers focus on companies outside of the typical motor carrier, like HAZMAT, Passenger and Bus Carriers.
CNS is part of a group of companies that offer other necessary services for the trucking and transportation industry, such as Commercial Trucking Insurance, CDL Training, Online Training Course, and even Healthcare.
Our DOT Licensing Services will cover you whether you are an existing company or just starting a trucking company. Our DOT Licensing Specialists can help you get up and running and in days with your DOT number, MC Authority, EIN, UCR, IFTA, 2290 HVUT, Fuel Taxes and can even set you up to get your Commercial Driver's License (CDL) with CNS Driver Training Center.
Our DOT Licensing Specialists will help you with every aspect of starting a trucking company. All you need to do is choose a name for your trucking company.
You will need to ensure your DOT Number, MC Authority, Vehicle Registration, etc. is all set up properly when you start your trucking business.
Our Licensing Specialists can help with all aspects of filing and renewing licenses, fuel taxes, etc.
CNS is part of a group of companies that offer other necessary services for the trucking and transportation industry, such as Commercial Trucking Insurance, CDL Training, Online Training Course, and even Healthcare.
To prevent reintroduction of rabies carried by dogs into the United States, new CDC regulations require proof of healthy pets at border crossing. Truckers who
CNS or Compliance Navigation Specialists is DOT Compliance company that assists trucking and transportation companies remain DOT Compliant. We are part of a network of companies, CNS Companies, specializing in services related to the transportation, manufacturing, construction, service, education and medical industries.
CNS Companies is a network of companies specializing in services related to the transportation, manufacturing, construction, service, education and medical industries. Our DOT Compliance division is handled by Compliance Navigation Specialists, CNS Insurance handles Commercial Truck Insurance, CDL training is managed by the CNS Driver Training Center and healthcare is managed by CNS Occupational Medicine.

FMCSA said none of its internal systems were compromised but advises that everyone who uses its portal to change their passwords immediately.
The Federal Motor Carrier Safety Administration has confirmed that an outside group known as KillNet has been trying to access its public portal using stolen user passwords.
The agency uses 13 web-based applications, to aid vehicle registration, inspections, compliance monitoring and enforcement. Many of FMCSA’s information systems contain sensitive data, including personally identifiable information.
As seen by Hackread.com, the hacker group claimed to have broken into the FMCSA’s public portal.
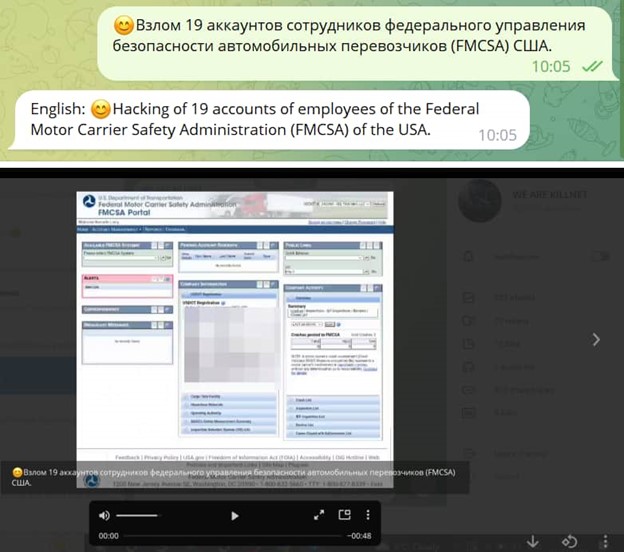
“While KillNet’s attacks usually do not cause major damage, they can cause service outages lasting several hours or even days,” according to an alert. “The group should be considered a threat to government and critical infrastructure organizations, including healthcare.”
In addition, Killnet said it had infiltrated the FBI’s database, allegedly stealing the personal information of more than 10,000 U.S. federal agents, the White House websites, and temporarily took down SpaceX’s Starlink satellite service used in Ukraine to help defend the country and maintain stable communications.
FMCSA is advising everyone who uses its portal to change their passwords immediately.
Back in October 2021, an audit concluded that FMCSA’s IT infrastructure was fraught with security weaknesses and was at risk by hackers and malware.
“We found several agency web servers which allowed us to gain unauthorized access to FMCSA’s network,” the audit said. “FMCSA did not detect our access or placement of malware on the network in part because it did not use required automated detection tools and malicious code protections.”
“We also gained access to 13.6 million unencrypted personally identifiable information records,” auditors said. “Had malicious hackers obtained this PII, it could have cost FMCSA up to $570 million in credit monitoring fees.”
FMCSA agreed with the audit’s 13 recommendations and planned to fix them by November 2022. According to the report, all 13 recommendations had been completed.
This may have helped prevent further damage by Killnet’s attempt to access the FMCSA portal.
FMCSA is advising everyone who uses the FMCSA portal to change their passwords immediately.
FMCSA’s security policies and processes must adhere to departmental policies and National Institute on Standards and Technology guidelines. This requires users to:

To prevent reintroduction of rabies carried by dogs into the United States, new CDC regulations require proof of healthy pets at border crossing. Truckers who

This means future regulations will “become clearer” or “stuck in the courts” for years. On June 28, 2024, the U.S. Supreme Court overturned the Chevron

ATRI’s Research Advisory Committee (RAC) selected a diverse set of research priorities designed to address some of the industry’s most critical issues including workforce development,

CNS can help with our Roadside & Incident Report Management service where a team of DOT Compliance Specialists will assess the Department of Transportation safety records
Our DOT Compliance Programs ensure it is your top priority and keeps your business running.
Receive the latest transportation and trucking industry information about FMCSA and DOT Audits, Regulations, etc.

To prevent reintroduction of rabies carried by dogs into the United States, new CDC regulations require proof of healthy pets at border crossing. Truckers who

This means future regulations will “become clearer” or “stuck in the courts” for years. On June 28, 2024, the U.S. Supreme Court overturned the Chevron

ATRI’s Research Advisory Committee (RAC) selected a diverse set of research priorities designed to address some of the industry’s most critical issues including workforce development,
Join our monthly newsletter and stay up-to-date on trucking industry news and receive important compliance and licensing tips.
Join our monthly newsletter and stay up-to-date on trucking industry news and receive important compliance and licensing tips.